New research used 3D printing technology to bypass fingerprint scanners, and tested it against Apple, Samsung and Microsoft mobile products.
New research has found that it’s possible to use 3D printing technology to create “fake fingerprints” that can bypass most fingerprint scanners used by popular devices. But, creating the attack remains costly and time-consuming.
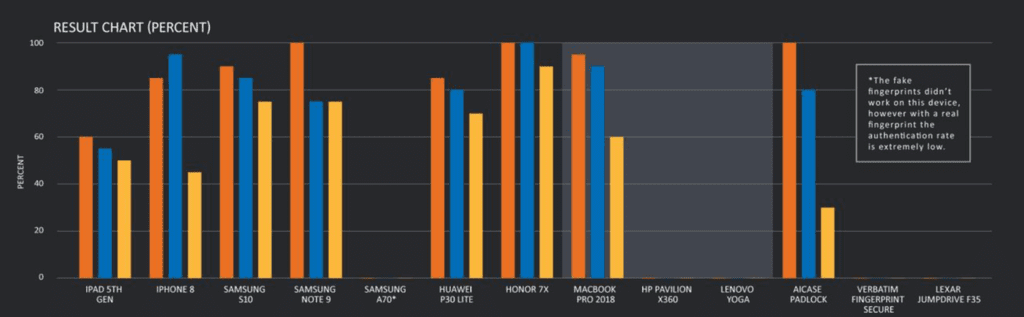
Researchers with Cisco Talos created different threat models that use 3D printing technology, and then tested them on mobile devices (including the iPhone 8 and Samsung S10), laptops (including the Samsung Note 9, Lenovo Yoga and HP Pavilion X360) and smart devices (such as a smart padlock).
The fake fingerprints achieved an 80 percent success rate on average, where the sensors were bypassed at least once. Researchers did not have success in defeating biometrics systems in place on Microsoft Windows 10 devices (though they said that this does not mean they are not necessarily safer; just that this particular approach did not work).
However, the bigger takeaway is the sheer amount of time and budget that it still takes when creating threat models to bypass fingerprint sensors. At the end of the day, researchers said they had to create more than 50 molds and test them manually, which took months – and, they struggled to stay under a self-imposed budget of $2,000. These challenges point to the fact that a scalable, easy type of attack is not yet possible for bypassing biometrics.
“Biometrics are not an Achilles heel,” Craig Williams, director of Cisco Talos Outreach, told Threatpost. “Biometrics are something that makes it very, very easy to use. You don’t have to remember a password. You don’t have to enter a password, which makes it very fast and easy. You don’t have to carry anything around with you. And so I think for most users, it’s still perfectly fine.”